Professional Security Services for Predictable, Reliable Outcomes
Advisory leadership with vCISO and vCIO, plus Assurance services including GLBA, FFIEC, and HIPAA audits, penetration testing, program roadmaps, and pragmatic IT and security consulting.

Advisory Services
Leadership and guidance that align technology with business outcomes.
Virtual CISO (vCISO)
Fractional security leadership to build, run, and mature your security program, meet regulatory expectations, and communicate risk in business terms.
Virtual CIO (vCIO)
Strategic IT planning, budgeting, vendor governance, and roadmap execution that keep operations stable and enable growth.
Interim / On‑Demand CISO
Keep momentum while you recruit. Flexible monthly leadership or pre‑purchased hours for surge support.
Program & Roadmap Development
Prioritized, budget‑ready roadmaps and policies that satisfy auditors and keep your teams focused on the highest‑value work.

Testing, Assessment, and Audit Services
Security‑first, regulator‑ready assurance to validate controls and close gaps.
Ransomware Gap Assessment
Assess against NIST IR 8374 to prevent, respond to, and recover from ransomware. Receive a prioritized remediation plan.
Penetration Testing
Internal and external testing of networks, applications, and cloud environments to uncover exploitable vulnerabilities and validate control effectiveness.
Risk Assessments
Tailored assessments for HIPAA, GLBA, FFIEC, SWIFT, and FERPA to identify exposure and guide remediation with clear owners and timelines.
Compliance Audits & Attestations
Independent reviews against GLBA, FFIEC, HIPAA, and internal policy to document effectiveness, satisfy regulators, and inform boards.
“TorchLight has been more than a vendor to our multi‑branch credit union; they’re a partner. We started with a security assessment and gap analysis in 2007 and have continued to grow with their guidance across strategy, compliance, and operations.”
– Annette, CEO
Why TorchLight?
We lead with service, clarity, and accountability. Expect candid guidance, proactive communication, and a security‑first mindset that aligns IT with business outcomes. Our team partners with yours to set priorities, execute the plan, and keep auditors and boards confident.
The Way Forward – TorchLight Blog
-

NCUA’s AI Compliance Plan: What It Signals for Credit Unions (and How to Get Ahead of It)
Artificial intelligence is moving from “innovation project” to operational reality across financial services. Regulators are responding the way they always do when a technology starts touching mission critical decisions: by building governance, documenting controls, and raising expectations for transparency and accountability.
-

The Year Systems Broke and Why 2026 Demands Action
If you assumed your security controls were working in 2025, you weren’t alone. So did 99% of defense contractors who failed CMMC compliance. So did organizations running on AWS when a 15-hour DNS error took down their operations.
-
Payment Remittance Phishing Attacks Security Bulletin
Over the past several days, the TorchLight Security Operations Center has observed a rapid escalation in payment remittance phishing attacks targeting end users across multiple industries. While these phishing techniques aren’t new, the scale and frequency of this week’s activity represent a significant shift in threat actor behavior. In this post, we break down what…
-
What Palo Alto’s Breach Teaches About Protecting SaaS Applications
In August, Palo Alto Networks got breached. Not through their firewall. Not through phishing. Through a Salesforce integration. Over 700 organizations were affected. And their security tools never saw it coming.
-
Strategic Guidance – Getting The Most From Your Pen Test Report
It’s Q4 and pen test reports are piling up. Most companies scan for critical findings, patch them, and move on. But those medium and low-risk findings everyone ignores? They’re revealing where your security posture is quietly deteriorating. Gary Blosser, our vCISO and Principal Security Architect, shows you how to extract real value from every section…
-
Docusign Phishing Attacks Security Bulletin
The TorchLight Security Operations Center has seen a massive increase in fake Docusign phishing emails since Monday of this week. While these threat vectors has been in use since early 2024, the massive rise in attacks this week is real. At this point, consider all Docusign emails to be hostile and must be carefully reviewed…
-
The Palo Alto Paradox: Why Even Security Giants Fall Through Integration Gaps
Recently, Palo Alto Networks fell victim to a cyber-attack. Attackers used compromised OAuth tokens to breach 700+ organizations through a third-party marketing tool integration. If a security giant like Palo Alto can fall through integration cracks, what does that say about your exposure?
-

The Future of Authentication: Why Phishing-Resistant MFA Matters
MFA fatigue is creating security gaps as employees mindlessly click “approve” on authentication prompts. Learn how phishing-resistant MFA eliminates password frustration while stopping credential-based attacks entirely. Augusto Melo explores why this strategic shift cuts breach risk, boosts productivity, and positions organizations ahead of compliance requirements.
-
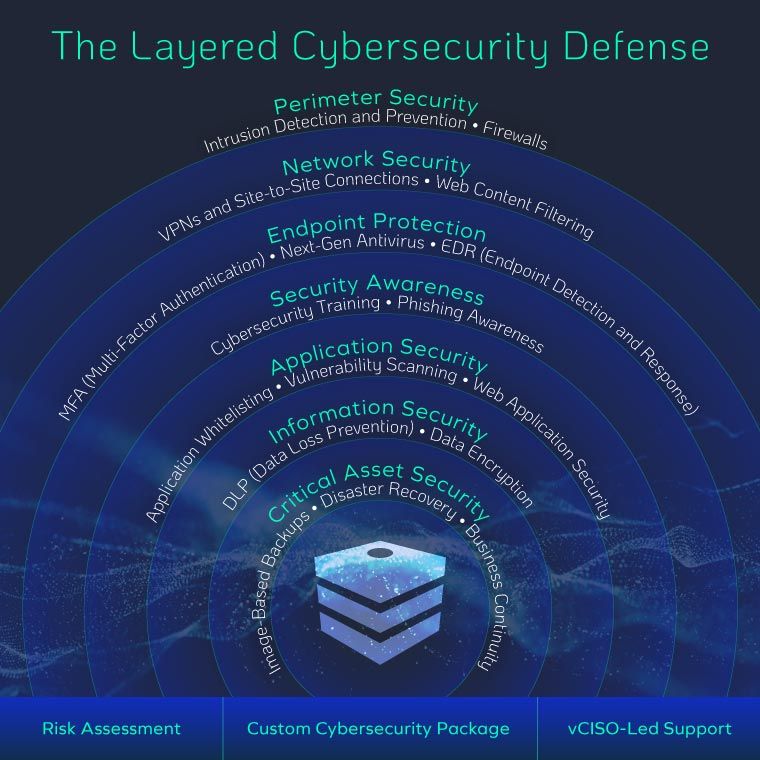
Why Advanced Cybersecurity Tools Still Fail – And What to Do Instead
It seems like every week another well-known company falls victim to a cyberattack—even those armed with the latest, most expensive cybersecurity tools. So why do breaches keep happening? After 15 years of breach investigations, one pattern is clear: most organizations lack a holistic approach to security. Tools are important, but without layered defenses—spanning prevention, detection,…
-

Why We Partnered with Drip7 Security Awareness Training to Tackle the Real Cybersecurity Risk: People
TorchLight has partnered with Drip7 to strengthen human-focused cybersecurity training. Learn how this microlearning platform helps reduce human error, improve security awareness, and support a holistic cybersecurity strategy for your business.
