Every week we hear about another major organization falling victim to a cyberattack. Many of these companies already have some of the most advanced and expensive security tools money can buy. Next-gen firewalls, AI-powered threat detection, endpoint protection, cloud security platforms, and the list goes on.
Yet breaches keep happening. Global reports show that despite billions invested in cybersecurity, the number of successful attacks and ransomware incidents continues to climb. This ongoing challenge highlights the increasing need for new cybersecurity approaches.
So, what is the disconnect?
After nearly 15 years of investigating breaches and helping businesses strengthen their defenses, we have seen one recurring problem: a lack of holistic security.
Cybersecurity Is Like Healthcare
Think about cybersecurity the same way you think about healthcare:
- Prevention: Regular exercise, good nutrition, vaccines
- Protection: Early treatment when symptoms appear
- Recovery: Surgery, rehabilitation, or major interventions after a health crisis
When prevention and protection are skipped, recovery is longer, more painful, and more expensive.
We see the same pattern in breach investigations. Organizations either:
- Do not have the right barriers in place to keep attackers out
- Lack the ability to detect and contain intrusions quickly
- Assume they are “unbreachable” and fail to plan for disaster recovery
The results are costly. Replacing compromised infrastructure, restoring lost data, fighting legal battles, losing customers, dealing with regulators, and only then putting proper defenses in place.
There is a better way: a layered, comprehensive security strategy that covers every stage of a potential attack.
The 5 Elements of Holistic Cybersecurity
Holistic security is not about relying on one “silver bullet” product.
It is about protecting every stage of the threat lifecycle.
| Phase | Key Question | Cost of Neglect |
|---|---|---|
| 1. Proactive Security | How do we prevent attackers from getting in? | Low |
| 2. Reactive Controls | If they get in, how do we detect and isolate them? | Moderate |
| 3. Incident Response | Once found, how do we contain the threat? | High |
| 4. Disaster Recovery | How do we restore operations after damage? | Very High |
| 5. Lessons Learned | How do we stop it from happening again? | Very High |
The earlier you stop a threat, the less it costs in money, downtime, and reputation.
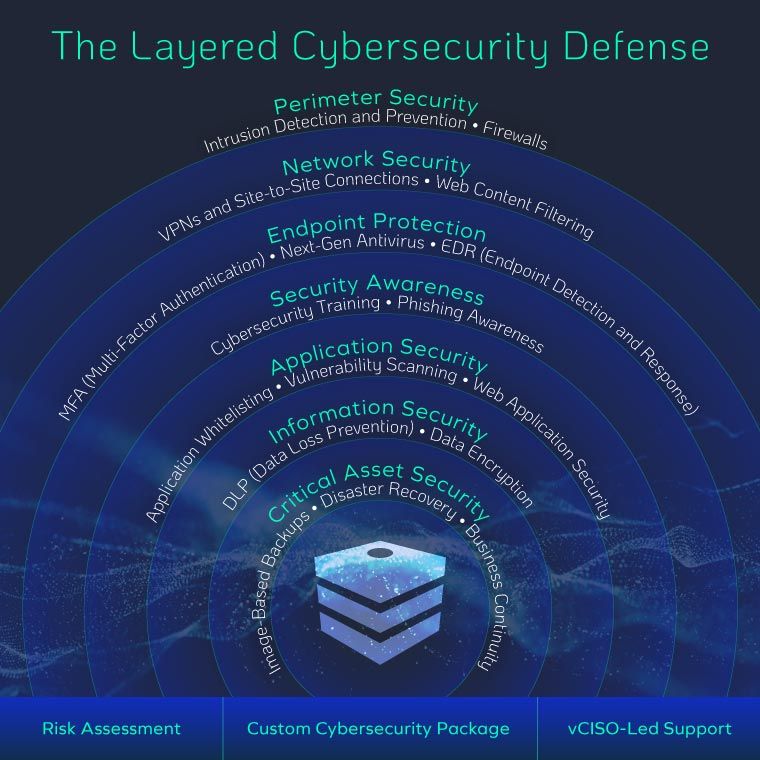
Breaking Down the Layers of Defense
Every business is different, but here is what a layered approach can look like.
1. Assessment and Discovery
You cannot protect what you cannot see.
- Vulnerability scanning: Find known weaknesses
- Penetration testing: Test how easily they can be exploited
- Tabletop exercises: Practice responding to a simulated attack
2. Proactive Security
Reduce your attack surface before attackers arrive.
- Application control: Only approved programs run
- DNS/Web filtering: Block malicious sites
- Privilege and access control: Give users only the access they need
3. Reactive Security Controls
Detect and contain threats quickly.
- EDR/Antivirus: Real-time detection of malicious behavior
- Ransomware isolation: Stop attacks mid-execution
- Identity threat detection: Catch compromised accounts
- SIEM correlation: Spot unusual patterns in activity
- 24/7 SOC: Constant monitoring and rapid response
4. Disaster Recovery and Insurance
Be ready for the worst-case scenario.
- Reliable backups: Restore systems and data quickly
- Cyber insurance: Financial support for major incidents
5. Lessons Learned and Continuous Improvement
Turn incidents into action.
- Post-incident reviews
- Root cause analysis
- Stronger controls based on findings
- Training tailored to actual gaps
Final Thoughts: Prevention Costs Less Than Recovery
No organization is invulnerable. But those with a layered, holistic cybersecurity defense are far less likely to suffer major damage and will recover more quickly when something does go wrong.
Ask yourself:
- Are we investing in prevention, detection, response, and recovery equally?
- Are we testing our defenses in real-world scenarios?
- Are we learning from past incidents and improving?
Cybersecurity is not just about buying tools. It is about building a system that can withstand bad days without becoming a disaster.
Ready to Strengthen Your Security?
Cyber threats are evolving. There is no single product or quick fix that guarantees safety. Real resilience comes from balancing prevention, protection, and recovery.
We have helped organizations of all sizes identify gaps, build effective defenses, and reduce risk before an incident occurs.
We are offering a complimentary cybersecurity assessment to help you:
- Understand your current security posture
- Pinpoint weak spots across people, processes, and technology
- Get clear, actionable recommendations to improve security holistically
Contact us today to schedule your free assessment and start building a more resilient, cost-effective security strategy.