
Stop Email Spoofing Before It Reaches Your Customers
Defend your brand, protect your customers, and cut the risk of phishing attacks by over 92%!
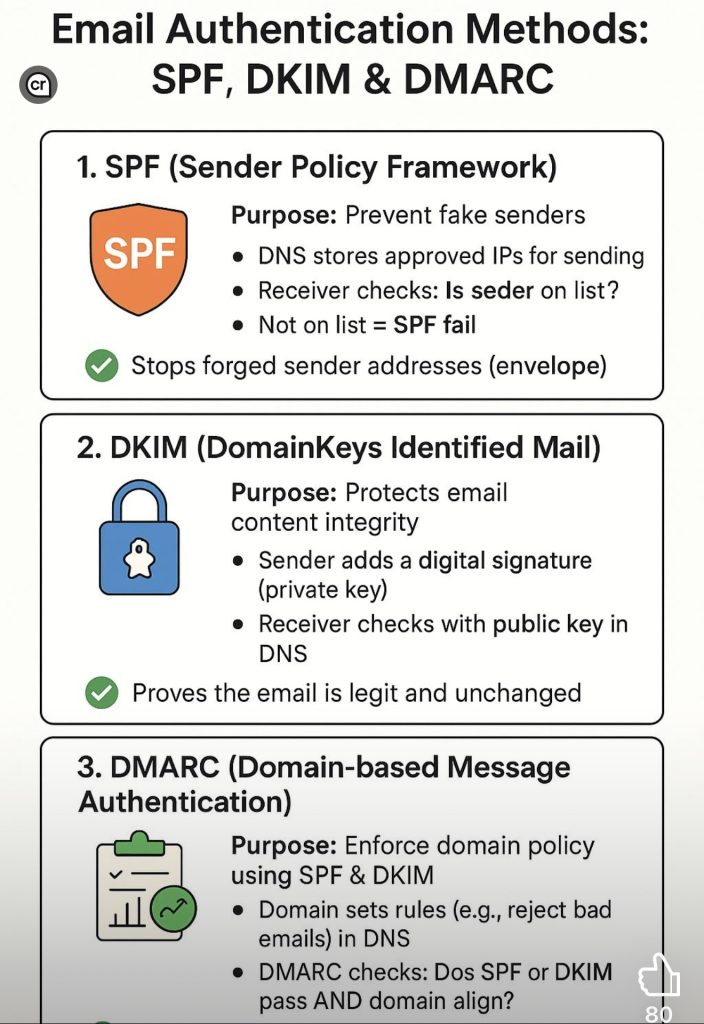
Why DMARC is essential for modern business email security
Every day, cybercriminals send millions of fraudulent emails that appear to come from legitimate businesses. These attacks damage customer trust, put your brand at risk, and can lead to financial and legal consequences.
DMARC (Domain-based Message Authentication, Reporting, and Conformance) is the industry standard for stopping these attacks before they reach inboxes. It works by verifying that emails sent from your domain are truly from you, blocking unauthorized senders, and giving you visibility into how your domain is being used.
Why DMARC matters:
Gives you actionable reports on domain activity
Protects your brand reputation
Blocks phishing and spoofing attempts
Increases email deliverability and trust
Gives you actionable reports on domain activity

Limited-Time Offer
For a limited time, get 50% off your DMARC service for the first 4 months when you sign up through this promotion.
Don’t wait until a phishing email damages your reputation. Secure your domain today and give your customers confidence that emails from you are legitimate.
Get Started and Claim 50% Off
The Way Forward – TorchLight Blog
-

Financial Institutions and Ransomware
Get ahead of attackers and protect valuable assets from impending ransomware attacks. Here are a few things that financial institutions should know about ransomware – its current trends, targets, and tactics.
-

Enterprise Business and Ransomware
The manufacturing industry has embraced automation and digitization as timelines have gotten tighter and business continuity has become essential. These aspects, along with the high-value data that manufacturing enterprises own (intellectual property, trade secrets, etc.) have made these types of companies more attractive cyber attack targets. Keep your supply chain running smoothly by protecting against…
-

Manufacturing and Ransomware
The manufacturing industry has embraced automation and digitization as timelines have gotten tighter and business continuity has become essential. These aspects, along with the high-value data that manufacturing enterprises own (intellectual property, trade secrets, etc.) have made these types of companies more attractive cyber attack targets. Keep your supply chain running smoothly by protecting against…
-

Healthcare and Ransomware
For the past several years, healthcare systems and hospitals have been high-profile victims of ransomware and other attacks. Find out what vectors for ransomware the healthcare sector faces.
-

SUEX, Crypto, and Ransomware
This year, the cryptocurrency platform SUEX was the first to be identified and sanctioned by the U.S. Government for its role in the ransomware payment chain, but it will likely not be the last. Here’s what you should know about SUEX and other cryptocurrencies.
-

Email Security in Ransomware Defense
Email security is an essential first step in patching vulnerabilities and protecting your business from malware and ransomware threats.
-

The Evolution of Ransomware
Over the past 40 years, the threat of ransomware has grown exponentially from initial generalized threats to targeted and specialized takedowns. New technology and the organization of perpetrators have evolved, and ransomware demands have never been higher.
-

The Seven Steps in the Ransomware Kill Chain
Ransomware can be a large concern for businesses – it compromises resources critical to operation and locks them in an encrypted environment until a ransom is paid. While every business should be aware of ransomware, not all understand the many steps involved in a full attack.
-

Channel Daily News Podcast with TorchLight’s Bo Wheeler
Bo Wheeler, Chief Revenue Officer at TorchLight, recently appeared on the Channel Daily News podcast with Don Witt to speak about the company, its mission, and the cybersecurity protection it provides for its customers.
-

Current Trends in Ransomware
Ransomware has been around almost as long as companies, institutions, and governments have been reliant on customer and constituent data. But there are ups and downs in popularity, tactics, and targets that can affect your company’s risk profile.