AI & Workflow Automation
For Predictable Growth
Design, document, and automate the work that runs your business so it flows the same way, every time.

AI & Workflow Automation Services
From scattered tasks and manual rework to documented, automated workflows that support growth and compliance.
We work with platforms such as Microsoft Copilot, Power Automate, n8n and other automation tools, but we remain tool agnostic so the solution fits your systems, controls, and people.
What AI & Automation Change For Your Team
We help you move beyond one-off bots and scripts into reliable systems that free up capacity, improve accuracy, and make your operating model more predictable.
Process Discovery and Design
We map your current workflows, identify bottlenecks, and design a future state that reduces handoffs, errors, and rework while aligning with your controls.
Workflow Automation and Integration
We connect the tools you already own so data moves cleanly between systems and the right people are notified at the right time.
Copilot and M365 Enablement
We help your team get real value from Microsoft Copilot and related tools by aligning prompts, governance, and workflows with your daily work.
Human-in-the-Loop Guardrails
We design approvals, reviews, and controls into your automations so AI speeds up work without creating new risk.
Monitoring, Metrics, and Improvement
Dashboards and simple metrics show where automations save time and where the process still needs tuning so you keep improving over time.
Compliance and Risk Aligned Automation
For regulated industries we align automations with exam expectations, documentation needs, and your cyber and data governance requirements.
Why TorchLight for AI and Automation?
At TorchLight, we believe AI should make your business more predictable, not more chaotic. We focus on the systems that run your organization, then apply automation where it reduces noise and risk instead of creating new problems.
Our team blends IT, security, and business process expertise so your automations respect role-based access, audit requirements, and examiner expectations. We prioritize open communication and a partnership mindset so leaders stay in control of outcomes while we handle the technical details.
The result is a clear roadmap, documented workflows, and automations that support your people. You gain capacity, consistency, and confidence that critical processes will run even when key staff are out of office.
The Way Forward – TorchLight Blog
-
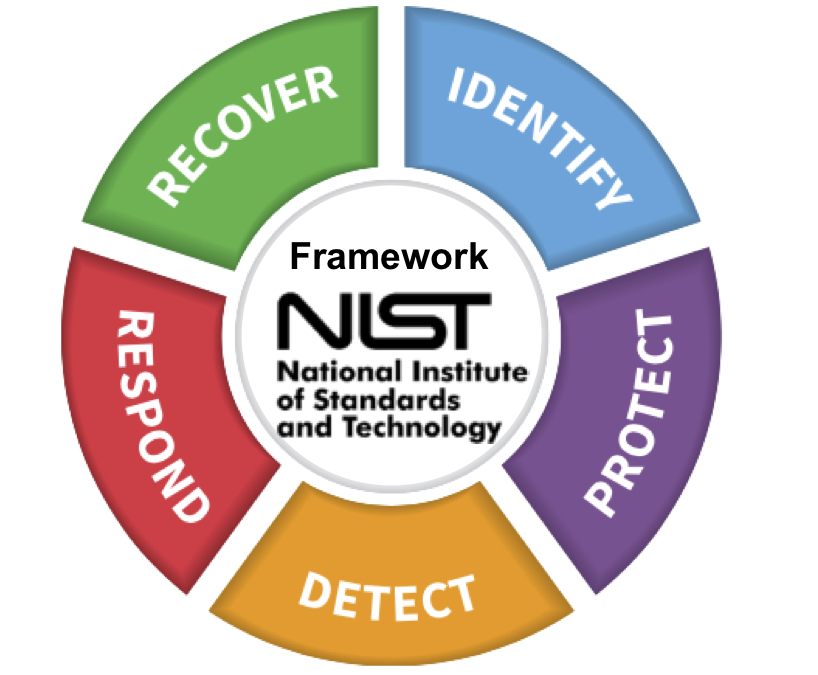
New NIST Guidelines Offer Starting Point for Cybersecurity
Important highlights about the National Institute of Standards and Technology (NIST) update of its guidance to organizations for assessing their internal security IT system.
-

Customer Testimonial: WETA
The proactive nature of the WETA’s leadership, spearheaded by Ken Jones (Senior Director, IT), drove WETA to form a partnership with TorchLight to ensure appropriate support for an infosec foundation as effective—and agile—as the ever-evolving threats and risks it faces.
-

Statement on Russia Cyberattacks
While we are aware of no specific or credible Russian cyber threats to the United States at this time, CISA recommends that organizations continue to be prepared to respond to any disruptive cyber activity.
-

Why Zero Trust is Essential for Remote Work
The rise of Zero Trust has helped businesses remain secure – even in remote working environments. Here are a few things that you should know about zero trust for your business and why it is essential for remaining cyber secure in both hybrid and remote workspaces.
-

Financial Institutions and Ransomware
Get ahead of attackers and protect valuable assets from impending ransomware attacks. Here are a few things that financial institutions should know about ransomware – its current trends, targets, and tactics.
-

Enterprise Business and Ransomware
The manufacturing industry has embraced automation and digitization as timelines have gotten tighter and business continuity has become essential. These aspects, along with the high-value data that manufacturing enterprises own (intellectual property, trade secrets, etc.) have made these types of companies more attractive cyber attack targets. Keep your supply chain running smoothly by protecting against…
-

Manufacturing and Ransomware
The manufacturing industry has embraced automation and digitization as timelines have gotten tighter and business continuity has become essential. These aspects, along with the high-value data that manufacturing enterprises own (intellectual property, trade secrets, etc.) have made these types of companies more attractive cyber attack targets. Keep your supply chain running smoothly by protecting against…
-

Healthcare and Ransomware
For the past several years, healthcare systems and hospitals have been high-profile victims of ransomware and other attacks. Find out what vectors for ransomware the healthcare sector faces.
-

SUEX, Crypto, and Ransomware
This year, the cryptocurrency platform SUEX was the first to be identified and sanctioned by the U.S. Government for its role in the ransomware payment chain, but it will likely not be the last. Here’s what you should know about SUEX and other cryptocurrencies.
-

Email Security in Ransomware Defense
Email security is an essential first step in patching vulnerabilities and protecting your business from malware and ransomware threats.
