
Credit Union Compliance Confidence
How One Credit Union Went From Cyber Insurance Cancellation to Zero NCUA Cybersecurity Findings in 90 Days
The step-by-step transformation that eliminated emergency IT calls during member service hours and restored board confidence.
Cyber Insurance Canceled
TorchLight received a phone call from a Credit Union CEO facing a crisis. Their insurance company had just canceled coverage following a failed NCUA audit and ongoing technical issues that disrupted member services. The final straw came when their failing firewall caused operational downtime on a payroll Friday.
The board was asking tough questions, but the CEO had been constrained by limited budget approval. Within 90 days, TorchLight transformed their operations.
- Upgraded their network infrastructure for bulletproof reliability
- Integrated previously ignored M365 licenses into daily business operations, including Teams, Outlook, SharePoint, and OneDrive
- Resolved all outstanding NCUA audit issues
- Restored the Credit Union to an insurable state

Secured & Managed IT by TorchLight
Our Secured & Managed IT Brings Board Actualization Through Our Maslow Heirarchy of Needs Approach To Credit Union Compliance Confidence:
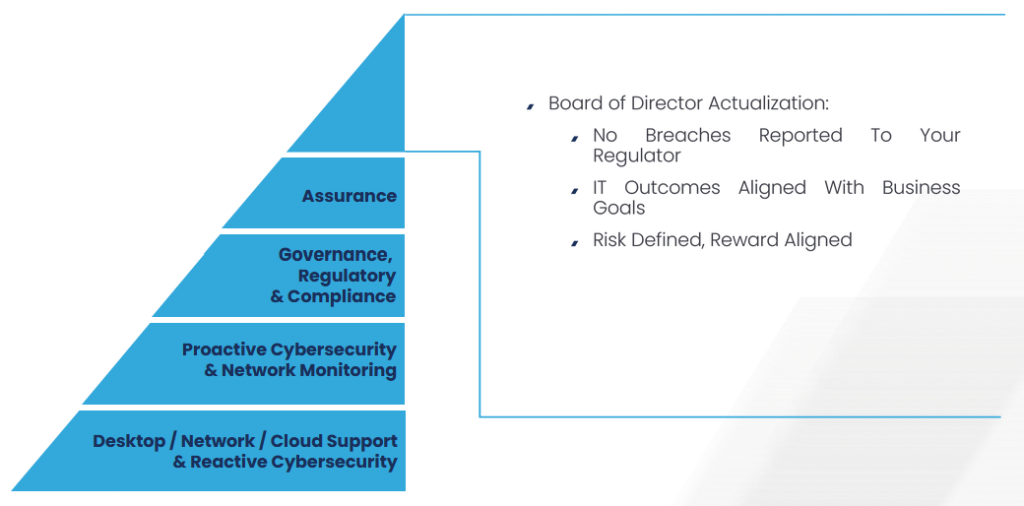
Board Actualization
- No Breaches To Report To Your Regulator
- IT Outcomes Aligned With Business Goals
- Risk Defined, Reward Aligned
Assurance
- Board Confidence That Controls And Oversight Actually Work
- If A Breach Were To Occur, Risk Communicated In Advance
- Act Swiftly To Recover, Contain Spread Immediately and Restore Operations Within Minutes
Governance, Regulatory and Compliance
- On Call Fractional Virtual Chief Information Security Officer
- Proactive Risk Awareness For Purpose Built Mitigations
- Board Level Reporting and Presentations By The vCISO
Proactive Cybersecurity and Network Monitoring
- 24/7/365 Human Powered Security & Network Operations Center
- DMARC, DNS and Email Spoofing Monitoring
- Desktop + Server Patching & Cloud + On-Prem Backups
- Customizable Security Awareness Training
- Dedicated Organizational Password Manager
- Integration with HR, Physical Access and Other Critical Systems
Desktop / Network / Cloud Support and Reactive Cybersecurity
- Patching + Backups
- Endpoint Detection + 24/7/365 Managed Incident Response
- Cloud Identity Detection + 24/7/365 Managed Incident Response
- Microsoft 365 Tenancy & License Management
- Predictable and Reliable Service Desk with Guaranteed SLA’s
What To Expect Working With TorchLight
Before: Downtime, user friction, customer headaches, technical debt, compliance dread.
After: Zero downtime, simplified business processes, increased compliance accountability with a predictable monthly budget.
We get Credit Unions. With more than 17 years of Managed Security & IT experience, along with testing, audits and consulting experience, we know what it takes to bring Board Self Actualization!
- Smooth on-boarding with a gradual implementation plan
- On Call vCISO to advise, consult and speak to your IT risks and help build Board awareness
- Predictable monthly cost that scales with confidence when it’s time to grow
- Maximize the value and full benefits with your M365 licensing
- Technical Liaison with your Processors, Integrators and Vendors
Get a Cybersecurity Compliance Assessment From a Certified Microsoft Solutions Partner for Security to Upgrade Your Credit Union to a Better Secured & Managed IT State with Compliance Confidence.
Why TorchLight?
At TorchLight, our “why” is simple: we exist to serve our customers and protect them from the relentless threat of hackers. This mission drives everything we do, setting us apart in the Secured and Managed IT landscape.
We foster a culture of candor, transparency, service, proactive communication and a growth mindset, all aimed at supporting our clients’ needs. We seek trusted partnerships with organizations that share our values, prioritizing open dialogue and a win/win mindset.
Together, we ensure that IT security goals are not only met but exceeded, safeguarding business continuity every day. Our people are our greatest asset, unified by our mission to secure and serve our customers and frustrate the hackers.
The Way Forward – TorchLight Blog
-
The Windows 10 to Windows 11 Transition
Another large milestone looms in the Microsoft ecosystem as Windows 10 is (mostly) officially sunsetted on October 14, 2025. Meaning, no new security updates will be produced by Microsoft, unless you purchase an ESU/Extended Security Update license for up to three years that will allow Windows 10 to continue receiving security updates on a regular…
-
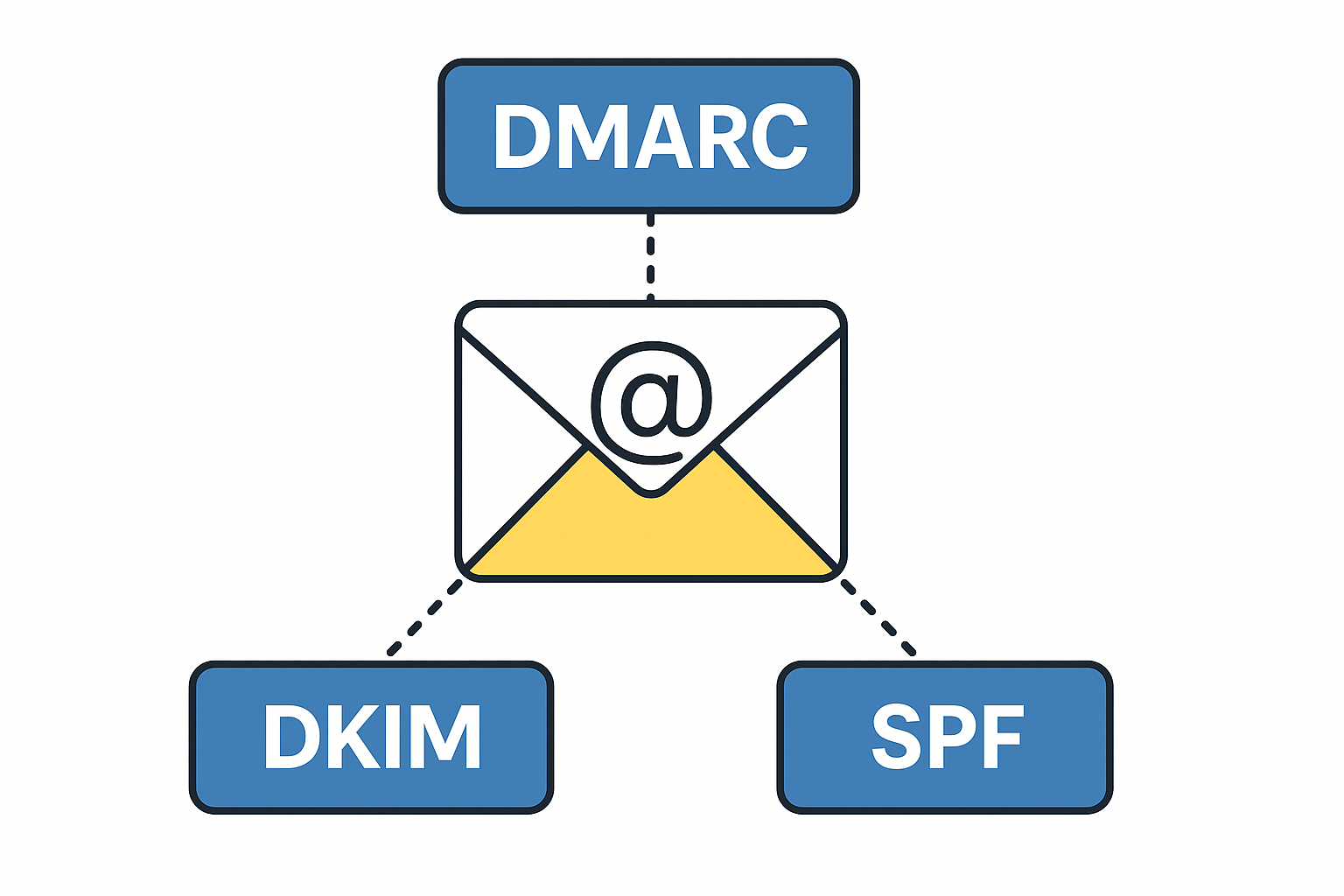
Tech Talk – What is DMARC, DKIM, SPF & Why Do I Want To Know?
DMARC, DKIM and SPF are three separate email authentication protocols that build layers of security around email delivery and integrity. Used in conjunction with each other, they provide a durable layer of protection for inbound emails and brand protection to prevent bad actors from sending emails using your business domain name. These tools provide domain…
-
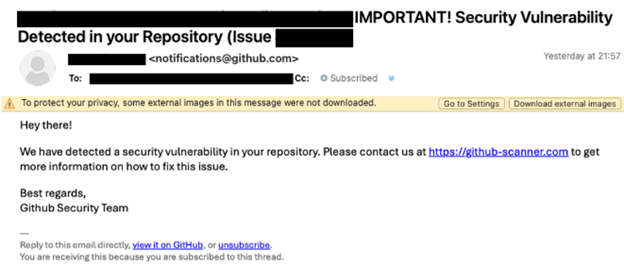
Beware of the ClickFix Scam!
TorchLight’s Threat Intelligence team has uncovered a resurgence of a phishing scam called ‘ClickFix,’ initially identified in late 2024 but now widely used by cybercriminals in 2025.
-

Microsoft Teams Phishing Attacks
TorchLight Security Operations Center continues to hear about Microsoft Teams as the vector to social engineering, phishing and spearphishing attempts by hackers. Given the volume of noise, we thought we’d publish what we know and how to defend against these attacks.
-

New Mac Vulnerability – Banshee MacOS Stealer
Our security operations center was notified of a new and novel bug that can affect all Macs. Titled “Banshee MacOS Stealer”, this first came on the scene in mid-2024 as a “malware as a service” exploit.
-

NIST Cybersecurity Framework 2.0 – Considerations for Small to Medium Sized Businesses
The NIST Cybersecurity Framework is a methodology designed to simplify the process of planning, implementing, managing and responding to threats from a holistic point of view in the Information Technology Delivery and Security space. It is specifically designed for organizations that either have no or very little cybersecurity planning, processes or responses to emerging threats.
-

Industry Impact of Ransomware Attacks
Find out why academic institutions, automobile dealerships, and the utility sector are all high-profile targets of ransomware attacks.
-

Employee Training & Email Security
Find out why employee training is essential for maintaining email security and protecting your business.
-

What to Know About Email Security
One of the weakest links in keeping your business secure can be the employee who opens a malicious email. Attack vectors get more and more sophisticated every day. That is why having up-to-date email security should be a top priority for your business.
-
New NIST Guidelines Offer Starting Point for Cybersecurity
Important highlights about the National Institute of Standards and Technology (NIST) update of its guidance to organizations for assessing their internal security IT system.