Managed IT & Security for Banks
Examiner-ready IT, resilient operations, and predictable cost—purpose-built for community and regional banks
What keeps bank CEOs up at night
- IT exam findings and documentation gaps
- Month-end/core downtime impacting customers and reporting
- Cyber-insurance renewals requiring fast maturity gains
- Vendor finger-pointing across core, LOS, online banking, and MSPs
- Board pressure for clearer cyber risk visibility
Outcomes TorchLight delivers
- Examiner-ready policies, evidence, and reporting cadence
- 99.9%+ uptime targets during critical banking hours
- Mapped controls that support cyber-insurance underwriting
- Single accountability across vendors, with direct escalation
- Board/committee-ready dashboards and QBRs
Regulator Approved, Security-Focused IT for Community Banks
Friendly service desk support, endpoint security, patching, backups, and cloud productivity are the basics. We implement them consistently so your business stays secure and operational, without slowing your team down.
Endpoint Detection and Response
Lightweight protection that monitors in real time, quarantines threats, and auto-remediates—without interrupting your day.
Vulnerability Management and Patching
Automated OS and app updates happen after hours to reduce disruption and close security gaps quickly.
Reliance Backups
Disaster-recovery-ready backups for workstations, servers, and cloud data—including M365 email and SharePoint.
Microsoft 365 Support
Simplified administration for email, identities, SharePoint, and Azure AD—managed in one pane of glass by our team.
24x7x365 Security Monitoring
We watch your business 24×7 and protect you in real time from threat actors.
Identity Threat Detection and Response (ITDR)
ITDR protects your business by monitoring and responding to suspicious account activity to keep user identities and data secure.
Examiner-Aligned, Operations-Ready
Examination readiness: policies, procedures, and evidence mapped to banking expectations; pre-exam reviews and remediation plans.
Operational resilience: monitoring and maintenance windows aligned to banking hours; month-end change freezes and test plans.
Vendor oversight: coordinated escalation with core/LOS/online banking; due-diligence evidence maintained for committees.
Cyber-insurance support: control implementation plans and attestations to help stabilize renewals.
Board visibility: QBRs and scorecards that translate IT risk to business impact and next actions.
Identity & access controls: MFA, SSO, conditional access, and privileged account vaulting with approvals and logging.
Endpoint & server protection: managed AV/EDR, patching, and configuration baselines with 24/7 response.
Backups & recovery: Reliance Backups for endpoints, servers, and M365 with tested restores.
Secure collaboration: hardened M365 tenants, secure file sharing, and mobile device management.
Incident response: named handlers, rapid containment, forensic coordination, and post-incident reporting.
Quiet and Safe IT for Your Community Bank
AV/EDR, patching, backups, identity, secure collaboration—these are the minimums. We implement them consistently, prove they’re working, and keep them aligned to your operating calendar.
Antivirus/EDR
Continuous detection and response with automatic quarantine and remediation—kept lightweight to avoid teller-line slowdowns.
Vulnerability Management
After-hours OS and app updates to close vulnerabilities without disrupting branch or wire desks.
Business Continuity and Disastery Recovery
DR-rated protection for endpoints, servers, and cloud data (M365 email/SharePoint) with periodic test restores and reports.
Microsoft 365 Hardening
Identity governance (MFA/SSO/conditional access), least privilege, and secure sharing—administered in one pane of glass.
Why TorchLight for Banks?
Because you need a partner that understands banking operations and examiner expectations, coordinates vendors without drama, and answers to your board with clarity. We deliver trust, security, and stability—so your team can grow deposits, make quality loans, and serve your community.
The Way Forward – TorchLight Blog
-
The Windows 10 to Windows 11 Transition
Another large milestone looms in the Microsoft ecosystem as Windows 10 is (mostly) officially sunsetted on October 14, 2025. Meaning, no new security updates will be produced by Microsoft, unless you purchase an ESU/Extended Security Update license for up to three years that will allow Windows 10 to continue receiving security updates on a regular…
-
Tech Talk – What is DMARC, DKIM, SPF & Why Do I Want To Know?
DMARC, DKIM and SPF are three separate email authentication protocols that build layers of security around email delivery and integrity. Used in conjunction with each other, they provide a durable layer of protection for inbound emails and brand protection to prevent bad actors from sending emails using your business domain name. These tools provide domain…
-
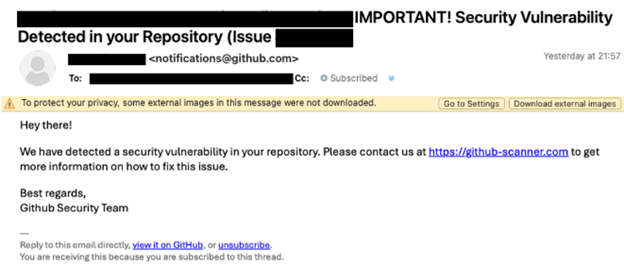
Beware of the ClickFix Scam!
TorchLight’s Threat Intelligence team has uncovered a resurgence of a phishing scam called ‘ClickFix,’ initially identified in late 2024 but now widely used by cybercriminals in 2025.
-

Microsoft Teams Phishing Attacks
TorchLight Security Operations Center continues to hear about Microsoft Teams as the vector to social engineering, phishing and spearphishing attempts by hackers. Given the volume of noise, we thought we’d publish what we know and how to defend against these attacks.
-

New Mac Vulnerability – Banshee MacOS Stealer
Our security operations center was notified of a new and novel bug that can affect all Macs. Titled “Banshee MacOS Stealer”, this first came on the scene in mid-2024 as a “malware as a service” exploit.
-

NIST Cybersecurity Framework 2.0 – Considerations for Small to Medium Sized Businesses
The NIST Cybersecurity Framework is a methodology designed to simplify the process of planning, implementing, managing and responding to threats from a holistic point of view in the Information Technology Delivery and Security space. It is specifically designed for organizations that either have no or very little cybersecurity planning, processes or responses to emerging threats.
-

Industry Impact of Ransomware Attacks
Find out why academic institutions, automobile dealerships, and the utility sector are all high-profile targets of ransomware attacks.
-

Employee Training & Email Security
Find out why employee training is essential for maintaining email security and protecting your business.
-

What to Know About Email Security
One of the weakest links in keeping your business secure can be the employee who opens a malicious email. Attack vectors get more and more sophisticated every day. That is why having up-to-date email security should be a top priority for your business.
-
New NIST Guidelines Offer Starting Point for Cybersecurity
Important highlights about the National Institute of Standards and Technology (NIST) update of its guidance to organizations for assessing their internal security IT system.
