Microsoft 365 Modern Workplace & Endpoint Security
Reduce complexity. Increase security. Give your team a simpler, safer way to work—anywhere.
TorchLight is your Microsoft 365 security-first partner. We design, migrate, and manage your modern workplace—then support your team every day.

The Modern Office with Microsoft 365
More secure. Less complex. No VPN for everyday work.
Simpler Day-to-Day
Single sign-on (Entra ID) & strong MFA
SharePoint/OneDrive instead of file servers
Teams for chat, meetings & voice
Stronger Security
Defender for Office 365 (anti-phish/spam)
Defender XDR for endpoints
Conditional Access & device compliance
Lower Complexity
Retire file/print servers & everyday VPN
Autopilot deployments & Autopatch
Cloud backup & continuity built-in
| Before (Legacy) | After with TorchLight M365 | |
| Access | VPN, shared drives | SharePoint/OneDrive, zero-trust |
| Devices | Imaging, GPOs | Autopilot + Intune |
| Security | Separate AV/spam/MDM | Defender XDR + Defender for O365 |
| Printing | Print servers | Universal Print |
| Updates | Manual patching | Autopatch + baselines |
Core Capabilities We Implement & Manage
Identity, devices, collaboration, protection, and automation—aligned to your risk profile.
Identity & Access
Entra ID (Azure AD), MFA, Conditional Access, SSO to apps.
Endpoint Management
Intune for Windows, macOS, iOS/Android with Autopilot & compliance.
Collaboration
Teams, SharePoint, OneDrive—reliable, secure collaboration without a VPN.
Protection
Defender XDR for endpoints & Defender for Office 365 for email threats.
Data & Printing
Purview DLP & sensitivity labels; Universal Print (serverless).
Automation
Autopatch, configuration baselines, and lifecycle policy enforcement.
Why TorchLight?
We exist to serve our customers and protect them from relentless cyber threats. We lead with transparency, proactive communication, and a security-first mindset—pairing Microsoft 365 expertise with day-to-day support and measurable outcomes.
The Way Forward – TorchLight Blog
-

Washington State Expands Sales Tax to IT Services
A new Washington State law—Senate Bill 5814—goes into effect on October 1, 2025, and it will significantly impact customers located in Washington who receive IT, digital, and tech-related services. This change will apply regardless of where the service provider is located, and may affect how your organization is billed by vendors like MSSPs, cloud providers,…
-
The Windows 10 to Windows 11 Transition
Another large milestone looms in the Microsoft ecosystem as Windows 10 is (mostly) officially sunsetted on October 14, 2025. Meaning, no new security updates will be produced by Microsoft, unless you purchase an ESU/Extended Security Update license for up to three years that will allow Windows 10 to continue receiving security updates on a regular…
-
Tech Talk – What is DMARC, DKIM, SPF & Why Do I Want To Know?
DMARC, DKIM and SPF are three separate email authentication protocols that build layers of security around email delivery and integrity. Used in conjunction with each other, they provide a durable layer of protection for inbound emails and brand protection to prevent bad actors from sending emails using your business domain name. These tools provide domain…
-
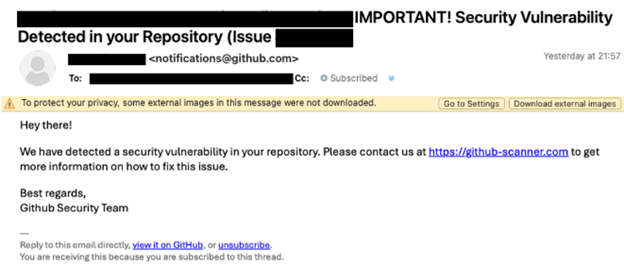
Beware of the ClickFix Scam!
TorchLight’s Threat Intelligence team has uncovered a resurgence of a phishing scam called ‘ClickFix,’ initially identified in late 2024 but now widely used by cybercriminals in 2025.
-

Microsoft Teams Phishing Attacks
TorchLight Security Operations Center continues to hear about Microsoft Teams as the vector to social engineering, phishing and spearphishing attempts by hackers. Given the volume of noise, we thought we’d publish what we know and how to defend against these attacks.
-

New Mac Vulnerability – Banshee MacOS Stealer
Our security operations center was notified of a new and novel bug that can affect all Macs. Titled “Banshee MacOS Stealer”, this first came on the scene in mid-2024 as a “malware as a service” exploit.
-

NIST Cybersecurity Framework 2.0 – Considerations for Small to Medium Sized Businesses
The NIST Cybersecurity Framework is a methodology designed to simplify the process of planning, implementing, managing and responding to threats from a holistic point of view in the Information Technology Delivery and Security space. It is specifically designed for organizations that either have no or very little cybersecurity planning, processes or responses to emerging threats.
-

Industry Impact of Ransomware Attacks
Find out why academic institutions, automobile dealerships, and the utility sector are all high-profile targets of ransomware attacks.
-

Employee Training & Email Security
Find out why employee training is essential for maintaining email security and protecting your business.
-

What to Know About Email Security
One of the weakest links in keeping your business secure can be the employee who opens a malicious email. Attack vectors get more and more sophisticated every day. That is why having up-to-date email security should be a top priority for your business.
