Professional Security Services for Predictable, Reliable Outcomes
Advisory leadership with vCISO and vCIO, plus Assurance services including GLBA, FFIEC, and HIPAA audits, penetration testing, program roadmaps, and pragmatic IT and security consulting.

Advisory Services
Leadership and guidance that align technology with business outcomes.
Virtual CISO (vCISO)
Fractional security leadership to build, run, and mature your security program, meet regulatory expectations, and communicate risk in business terms.
Virtual CIO (vCIO)
Strategic IT planning, budgeting, vendor governance, and roadmap execution that keep operations stable and enable growth.
Interim / On‑Demand CISO
Keep momentum while you recruit. Flexible monthly leadership or pre‑purchased hours for surge support.
Program & Roadmap Development
Prioritized, budget‑ready roadmaps and policies that satisfy auditors and keep your teams focused on the highest‑value work.

Testing, Assessment, and Audit Services
Security‑first, regulator‑ready assurance to validate controls and close gaps.
Ransomware Gap Assessment
Assess against NIST IR 8374 to prevent, respond to, and recover from ransomware. Receive a prioritized remediation plan.
Penetration Testing
Internal and external testing of networks, applications, and cloud environments to uncover exploitable vulnerabilities and validate control effectiveness.
Risk Assessments
Tailored assessments for HIPAA, GLBA, FFIEC, SWIFT, and FERPA to identify exposure and guide remediation with clear owners and timelines.
Compliance Audits & Attestations
Independent reviews against GLBA, FFIEC, HIPAA, and internal policy to document effectiveness, satisfy regulators, and inform boards.
“TorchLight has been more than a vendor to our multi‑branch credit union; they’re a partner. We started with a security assessment and gap analysis in 2007 and have continued to grow with their guidance across strategy, compliance, and operations.”
– Annette, CEO
Why TorchLight?
We lead with service, clarity, and accountability. Expect candid guidance, proactive communication, and a security‑first mindset that aligns IT with business outcomes. Our team partners with yours to set priorities, execute the plan, and keep auditors and boards confident.
The Way Forward – TorchLight Blog
-
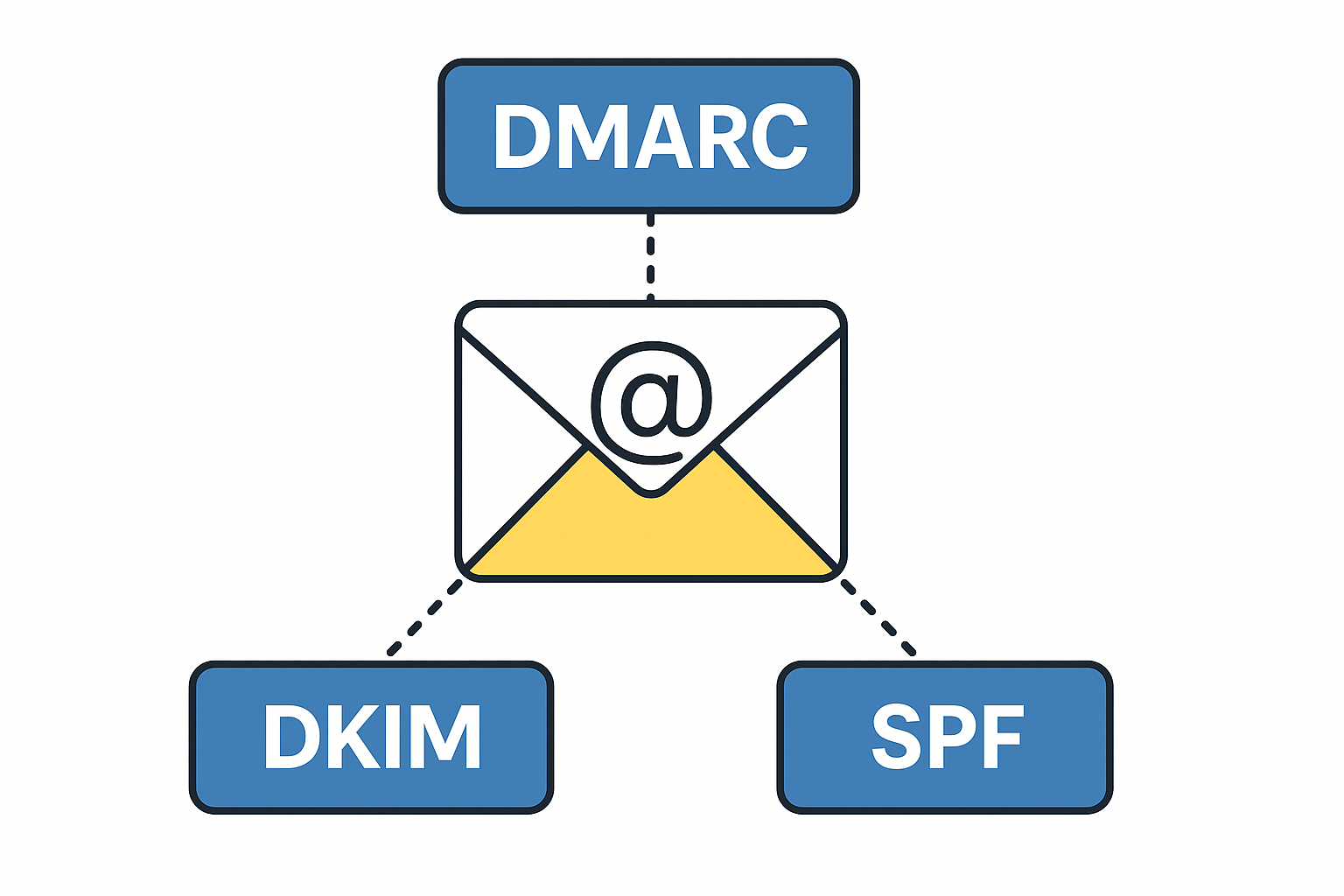
Tech Talk – What is DMARC, DKIM, SPF & Why Do I Want To Know?
DMARC, DKIM and SPF are three separate email authentication protocols that build layers of security around email delivery and integrity. Used in conjunction with each other, they provide a durable layer of protection for inbound emails and brand protection to prevent bad actors from sending emails using your business domain name. These tools provide domain…
-
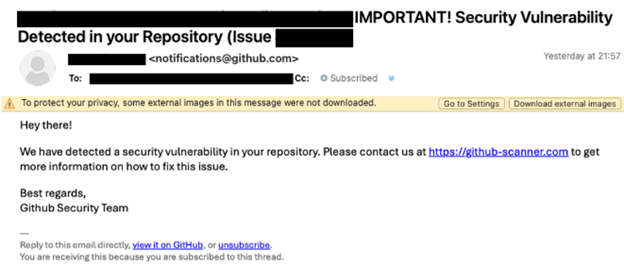
Beware of the ClickFix Scam!
TorchLight’s Threat Intelligence team has uncovered a resurgence of a phishing scam called ‘ClickFix,’ initially identified in late 2024 but now widely used by cybercriminals in 2025.
-

Microsoft Teams Phishing Attacks
TorchLight Security Operations Center continues to hear about Microsoft Teams as the vector to social engineering, phishing and spearphishing attempts by hackers. Given the volume of noise, we thought we’d publish what we know and how to defend against these attacks.
-

New Mac Vulnerability – Banshee MacOS Stealer
Our security operations center was notified of a new and novel bug that can affect all Macs. Titled “Banshee MacOS Stealer”, this first came on the scene in mid-2024 as a “malware as a service” exploit.
-

NIST Cybersecurity Framework 2.0 – Considerations for Small to Medium Sized Businesses
The NIST Cybersecurity Framework is a methodology designed to simplify the process of planning, implementing, managing and responding to threats from a holistic point of view in the Information Technology Delivery and Security space. It is specifically designed for organizations that either have no or very little cybersecurity planning, processes or responses to emerging threats.
-

Industry Impact of Ransomware Attacks
Find out why academic institutions, automobile dealerships, and the utility sector are all high-profile targets of ransomware attacks.
-

Employee Training & Email Security
Find out why employee training is essential for maintaining email security and protecting your business.
-

What to Know About Email Security
One of the weakest links in keeping your business secure can be the employee who opens a malicious email. Attack vectors get more and more sophisticated every day. That is why having up-to-date email security should be a top priority for your business.
-
New NIST Guidelines Offer Starting Point for Cybersecurity
Important highlights about the National Institute of Standards and Technology (NIST) update of its guidance to organizations for assessing their internal security IT system.
-

Customer Testimonial: WETA
The proactive nature of the WETA’s leadership, spearheaded by Ken Jones (Senior Director, IT), drove WETA to form a partnership with TorchLight to ensure appropriate support for an infosec foundation as effective—and agile—as the ever-evolving threats and risks it faces.
