Managed Security Services
For Proactive Cybersecurity
Proactive Blocking and Threat Hunting For Emerging Threats And Instant Active Remediation Response When A Threat Is Identified.

Our Managed Service Service Packages
Holistic IT Services to Design, Build and Manage to Achieve
Business Outcomes At A Predictable Per User Cost
Vigilance
Essential Security
Perfect for companies needing a fractional
security solution that partners with company internal IT staff, but without the expensive tooling and certified staffing requirements.
• 24/7/365 Security Operations Center (SOC) with active human monitoring
• Incident escalation upon detection to your
internal team for containment and mitigation
•Threat intelligence that exposes the
cyberattacker and their online infrastructure
Vigilance
Professional Security
Ideal for the larger enterprise customers and entities with regulatory and policy requirements.
• Vigilance Essential +
• Real Time Active Response and Incident
Management
• Threat hunting that seeks out threats before they land to prevent exploitation (and frustrate hackers).
• Weekly meeting availability
• Monthly SOC Reports
Vigilance
Ultimate Security
Our expanded service offering allows you to free up your team to focus on what they do best.
• Vigilance Professional +
• M365 Support and license management
• Vulnerability Management to monitor and
proactively fix known vulnerabilities found
within your network.
Managed Firewall
Our managed firewall service takes the
headache and worry from making sure your
ACL’s and policies match organizational
outcomes and goals.
This service includes firmware upgrades and vulnerability patching.
| 24/7/365 Active Monitoring | Incident Escalation | Threat Intelligence | Incident Containment | Active Response | Threat Hunting | M365 Support | Vulnerability Management | |
| Essential | √ | √ | √ | + | + | + | ||
| Professional | √ | √ | √ | √ | √ | |||
| Ultimate | √ | √ | √ | √ | √ | √ | √ | √ |
Security Incident Workflow
We utilize the NIST Cyber Security Framework to Integrate assets into a common logging and alerting platform and monitor, analyze and investigate IT threats.
Integration
Integration of cloud and on-premise SIEM tools with security endpoints.
Collection
Collection of cloud and on-premise user data, device, application and infrastructure log data.
Detection & Reporting
Detection and Reporting of prioritized threats with processes to root out false positives.
Investigation
Investigation of threats in real time to determine size and nature of the threat.
Containment & Eradication
Containment of the endpoint and/or identity to prevent further spread and eradication of all known vectors with strategic remediation to prevent follow up incidents.
Review
Review includes post-incident reports, lessons learned, root cause analysis and policy considerations.
Why TorchLight?
At TorchLight, our “why” is simple: we exist to serve our customers and protect them from the relentless threat of hackers. This mission drives everything we do, setting us apart in the Secured and Managed IT landscape.
We foster a culture of candor, transparency, service, proactive communication and a growth mindset, all aimed at supporting our clients’ needs. We seek trusted partnerships with organizations that share our values, prioritizing open dialogue and a win/win mindset.
Together, we ensure that IT security goals are not only met but exceeded, safeguarding business continuity every day. Our people are our greatest asset, unified by our mission to secure and serve our customers and frustrate the hackers.
The Way Forward – TorchLight Blog
-
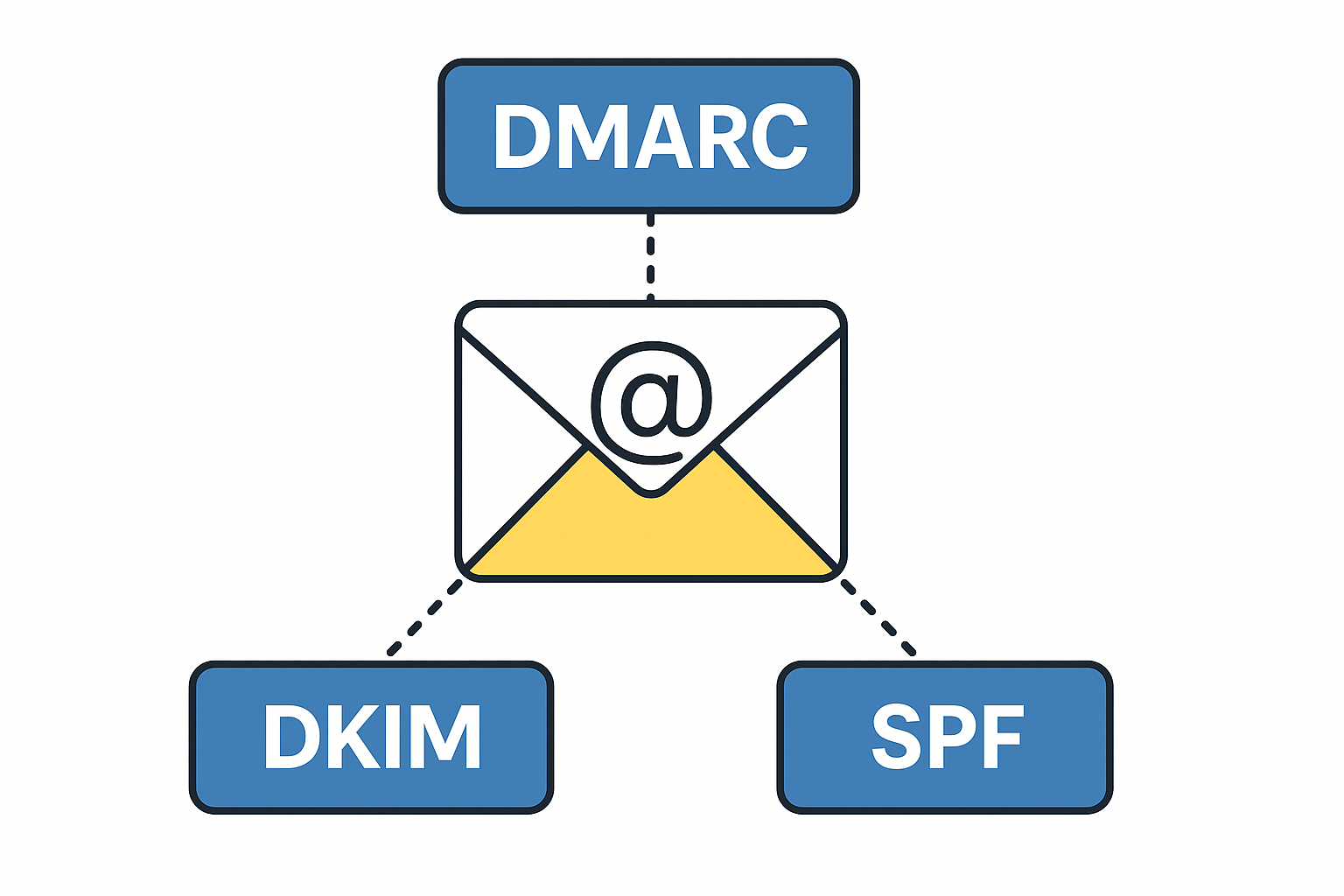
Tech Talk – What is DMARC, DKIM, SPF & Why Do I Want To Know?
DMARC, DKIM and SPF are three separate email authentication protocols that build layers of security around email delivery and integrity. Used in conjunction with each other, they provide a durable layer of protection for inbound emails and brand protection to prevent bad actors from sending emails using your business domain name. These tools provide domain…
-
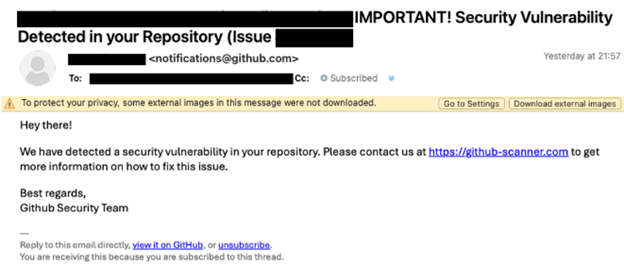
Beware of the ClickFix Scam!
TorchLight’s Threat Intelligence team has uncovered a resurgence of a phishing scam called ‘ClickFix,’ initially identified in late 2024 but now widely used by cybercriminals in 2025.
-

Microsoft Teams Phishing Attacks
TorchLight Security Operations Center continues to hear about Microsoft Teams as the vector to social engineering, phishing and spearphishing attempts by hackers. Given the volume of noise, we thought we’d publish what we know and how to defend against these attacks.
-

New Mac Vulnerability – Banshee MacOS Stealer
Our security operations center was notified of a new and novel bug that can affect all Macs. Titled “Banshee MacOS Stealer”, this first came on the scene in mid-2024 as a “malware as a service” exploit.
-

NIST Cybersecurity Framework 2.0 – Considerations for Small to Medium Sized Businesses
The NIST Cybersecurity Framework is a methodology designed to simplify the process of planning, implementing, managing and responding to threats from a holistic point of view in the Information Technology Delivery and Security space. It is specifically designed for organizations that either have no or very little cybersecurity planning, processes or responses to emerging threats.
-

Industry Impact of Ransomware Attacks
Find out why academic institutions, automobile dealerships, and the utility sector are all high-profile targets of ransomware attacks.
-

Employee Training & Email Security
Find out why employee training is essential for maintaining email security and protecting your business.
-

What to Know About Email Security
One of the weakest links in keeping your business secure can be the employee who opens a malicious email. Attack vectors get more and more sophisticated every day. That is why having up-to-date email security should be a top priority for your business.
-
New NIST Guidelines Offer Starting Point for Cybersecurity
Important highlights about the National Institute of Standards and Technology (NIST) update of its guidance to organizations for assessing their internal security IT system.
-

Customer Testimonial: WETA
The proactive nature of the WETA’s leadership, spearheaded by Ken Jones (Senior Director, IT), drove WETA to form a partnership with TorchLight to ensure appropriate support for an infosec foundation as effective—and agile—as the ever-evolving threats and risks it faces.
